Trend Micro IoT Security

Importance of Cybersecurity
A constantly changing world, including a global pandemic, have caused major shifts in how people conduct their daily lives. Working remotely has become more commonplace, thus vastly increasing online activity. Inevitably, businesses rely on computers, sensors, and IOT/IIOT connected devices more than ever, which also draws the attention of cyber criminals.
Maintaining good cybersecurity protection is crucial, especially for businesses and governments. VIVOTEK understands the importance of cybersecurity for products and corporations. Our quality assurance efforts are built into the lifecycle of our products, including development, verification, manufacturing, delivery, and service. We are constantly evaluating and enhancing our cybersecurity protection efforts in order to provide the highest quality and most reliable products.

Security Strengthened Product
As a leading supplier of surveillance cameras, VIVOTEK provides product lines with strengthened security settings to ensure customers safeguard their own security. VIVOTEK customers can breathe easier knowing that our products have undergone rigorous cybersecurity efforts for their protection.
Signed Firmware - VIVOTEK Authorized Firmware
VIVOTEK’s signed firmware requires a digital signature in the firmware and verification of the signature by VIVOTEK, thereby ensuring that users can trust the firmware has not been tampered with. A device with signed firmware can validate the firmware before allowing installation. By applying the signed certificates and keys to the firmware, quarantine that all data are secured and encrypted without any exposure and alter risk from hackers.
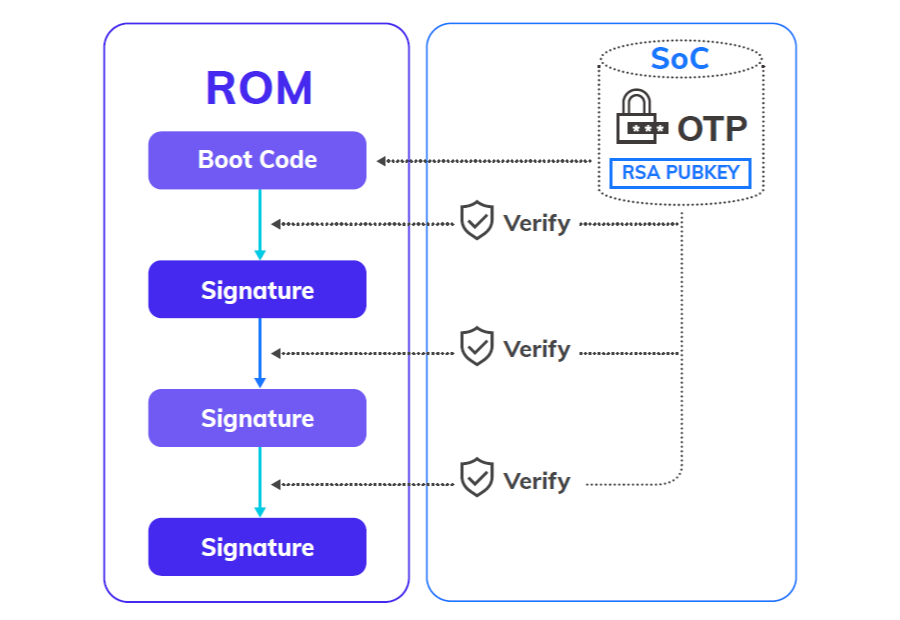
Secure Boot - Secure from the Beginning
By applying VIVOTEK’s signed firmware, the camera can securely startup step by step. Secure boot is a mechanism that protects the firmware of the product installed. During the boot up process, secure boot blocks unauthenticated or tampered code. Additionally, signed firmware ensures that camera restores safely to factory default, and secure boot ensures that unauthenticated code is rejected, protecting the camera system from attacks or infections by malicious external code.
Secure Console - Constant Protected Connection
On the basis of secure boot, we updated the remote access security mechanism and disabled the console of the camera from the SSH and SFTP protocol, which defends the vulnerability of the system. Permission from VIVOTEK with key based authentication is the only way to access, providing a safer connection for the surveillance system.

Secure VADP - Enhanced Security for 3rd Party Integration
VIVOTEK Application Development Platform (VADP) provides an open platform that enables developers to add on features for specific scenarios or applications with VIVOTEK’s cameras. Securing the VADP with enhanced security is critical. Applying Secure VADP with digital signature and encryption capabilities makes it safer and more reliable for third-party integration.

Collaborating in Cyber Protection
In collaboration with cybersecurity software partners, VIVOTEK focuses on making network security products and software that meet industry protocols as well as constantly developing shields to increase your protection from various cyberattacks. By choosing VIVOTEK solutions, users can experience not only high-quality products, but also safer network environments.
Cybersecurity Management

Alliance with Trend Micro

Understand Cyber Risks
Alliance with Trend Micro Cybersecurity
VIVOTEK is the world’s first network surveillance solution manufacturer to cooperate with the world-renowned cybersecurity company, Trend Micro. Through network cameras armed with Trend Micro's anti-intrusion software, VIVOTEK brings high security and robust network surveillance to secure lives and protect data.

Multi-Layer Protection with Trend Micro IoT Security
Multi-Layer Protection including Brute Force Attack Detection, Intrusion Detection and Prevention, and Instant Damage Control will automatically secure your network system with the latest signature upgrades.

Cybersecurity Alarm Management with Instant Alerts
Once event notifications in network cameras and VAST 2 VMS have been set up, VIVOTEK’s surveillance solution will be immediately alerted when cyberattacks occur.

Cybersecurity Event Report with Interactive Dashboard
Quickly know attack trend and status, and acquire attack information in order to diagnose your network promptly on VIVOTEK’s VAST 2 VMS and NVRs.
Instant Event Notifications

Brute Force Attack Events
When the system detects brute-force attacks, it will automatically activate a defense mechanism to block that IP address and prevent further attacks.

Cyberattack Events
When the system detects any kind of cyber security attack besides Brute Force Attacks, it will automatically activate a defense mechanism to block that IP address and prevent further attacks.

Quarantine Events
If a suspicious device tries to access the network, or if a suspicious device tries to access IP cameras, and accesses network behavior hitting the Trend Micro signature rule, the system will quarantine the attack behavior to prevent further damage.
Understand Your Cyber Risks
To safeguard the network, we encourage users to better understand the risks and apply the recommended solutions to reduce their vulnerabilities from cyberattacks:
- Use a strong password (Never use the default password).
- Download the latest firmware to fix bugs and vulnerabilities.
- Follow VIVOTEK's Vulnerability Policy to know how to manage and respond to security vulnerabilities.
- Implement VIVOTEK's Hardening Guide to secure basic, advanced, or enterprise infrastructures.
- Refer Security Advisories to help reduce risks of known vulnerabilities.

